| 6.1. Identify the Threat and Attack Vectors |
| 6.1.5. Upload to Anubis.iseclab.org |
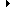 | 6.1.5.1. Does the executable modify critical files? |
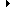 | 6.1.5.2. Does the executable modify common load points in the |
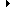 | 6.1.5.3. Does the executable open communications to the internet? and |